What happens to security with rise of quantum computers? How does AWS anticipate this revolution?
In this article we’ll have a glimpse in to the future by highlighting the possibility of pre-testing the security level of your applications before hackers will with more powerful computers. Securing internet connection via Transport Layer Security (TLS) is state of the art today. The key exchange with common algorithms takes place at the beginning of each session. Due to the strength of the used algorithms, hackers are unable to break the encryption – even with the strongest available computer of today. Nevertheless, the next generation of hardware – the quantum computers – will be a game changer. The rise of quantum computer will enable the hacking of public key cryptography schemes using Shor’s algorithm.
Important terminology
- Transport Layer Security (TLS): TLS is a security protocol for internet communication consisting of two components. The TLS Handshake is a key exchange between two systems, who want to communicate over the internet. Within TLS Record the key processed between the two systems encrypts the data. The algorithm used in the current version 1.3 of TLS is the Diffie-Hellman-protocol. The AWS environment uses S2N – an open-source implementation (see https://github.com/awslabs/s2n for more details).
- The Diffie-Hellmann protocol (DHP) named by the inventors Whitfield Diffie and Martin Hellman. For instance, Alice and Bob want to agree on a shared secret over an unsecure line. Eve can eavesdrop on that line, but cannot decipher the key in any reasonable time using current hardware. The key is created using functions that are easy to verify but hard to reverse. Alice and Bob each added their own secrets to the key, which are easy for the other to verify but impossible for Eve to decipher.
- Shors algorithm: Peter Shor created an algorithm in 1994, that can factor large integer numbers using features of quantum computing. For now, this is only theory as sufficiently specced quantum computes don’t exist. This will change, eventually. Today’s public-key-cryptography algorithms like DHP rely on the inability of convectional computers to efficiently factor large integers. Shors algorithm on quantum computers will enable the recovery of TLS recorded sessions and the readability of encrypted data using the calculated key. Shors algorithm is the starting point of research within the spectrum of cryptography algorithms a.k.a. post-quantum cryptography.
Key exchange in AWS environments
In June 2019, AWS introduced a new key exchange mechanism named „post-quantum cryptography for s2n” (https://github.com/awslabs/s2n/tree/main/pq-crypto). It introduces a hybrid key exchange combining two independent key exchanges, one for the classical world and one for the future quantum world.
Why is AWS introducing this now with no quantum computers around? Why should you think about adopting it? First, post-quantum cryptography for s2n today means better protection for your data. Second, you will be one step ahead of attackers. However, costs to bandwidth and latency will arise. Therefor, we recommend testing in your own environment with several resources being involved in a key exchange process. At this point, it’s important to mention that AWS is seeking to team up with customers for this matter. More infos here: https://aws.amazon.com/blogs/security/round-2-post-quantum-tls-is-now-supported-in-aws-kms/.
Within AWS environments, AWS Key Management Service (AWS KMS) is the central component of key management. More infos here: https://docs.aws.amazon.com/kms/latest/developerguide/overview.html. AWS KMS uses previous described Diffie-Hellman-Algorithm. Hardware security modules protect a customers master keys. AWS KMS integrates with most other AWS services, which require data encryption. If you are interested in building your own security applications, you can use SDKs for different programming languages to integrate AWS KMS in your application. The following link provides instructions about usage of AWS KMW in the event of hybrid post-quantum TLS: https://docs.aws.amazon.com/kms/latest/developerguide/pqtls.html.
Hybrid key exchange
There has been scientific research on the development and use of secure algorithms for the era of quantum computers for some time. The National Institute for Standards and Technology (NIST) coordinates these investigations. AWS is contributing by proposing a hybrid key exchange, which involves two key exchanges during the TLS handshake. The TLS session key is form by the cryptographically combination of both keys. The NIST standardization process is an ongoing process which most probably remains uncompleted until 2024. Therefore, you should not rely entirely on the new “post-quantum key” today. We recommend to use the proposed hybrid process with both keys (old and new).
Running your own tests
You eager to implement tests using the new post-quantum cipher suites with AWS KMS? Have a look at the developer previews of the Java SDK 2.0 (https://github.com/aws/aws-sdk-java-v2/tree/aws-crt-dev-preview) and the AWS Common Runtime. For instance, the following code snippet from https://aws.amazon.com/blogs/security/round-2-post-quantum-tls-is-now-supported-in-aws-kms/ illustrates the way you can build your tests:
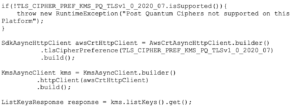
Integrating this snippet in your initialization code you can execute performance tests and check for blocked requests somewhere in your network. A complete source code example can be checked out here: https://github.com/aws-samples/aws-kms-pq-tls-example.
Conclusion
Hence, know for a fact that current key exchange procedures are vulnerable to quantum computers. Therefore, now is the time to look at the challenges large-scale quantum computing will bring to cryptography. AWS asks interested customers to work together to be one step ahead of potential attackers in the future.
If you need assistance assessing your situation do not hesitate to contact us.