This is the last part of our blog post series in which we describe a Gatekeeper implementation with templates and constraints over several clusters.
As we already know, Gatekeeper runs the Open Policy Agent that requires data and rules to decide which incoming API-Calls are valid or not. The template and constraint approach is an easy way of giving the Open Policy Agent the data foundation it needs to make those decisions.
Templates are a parametrized wrapper around rego code that allows outsourcing source code into external libraries. As the engine of Gatekeeper fetches the data for OPA from the state of the cluster, we can now use hardened external sources for our rego code. As a result, DevOps Team Members don’t need to learn a new language only to realize functions such as PSPs over Admission Controllers anymore.
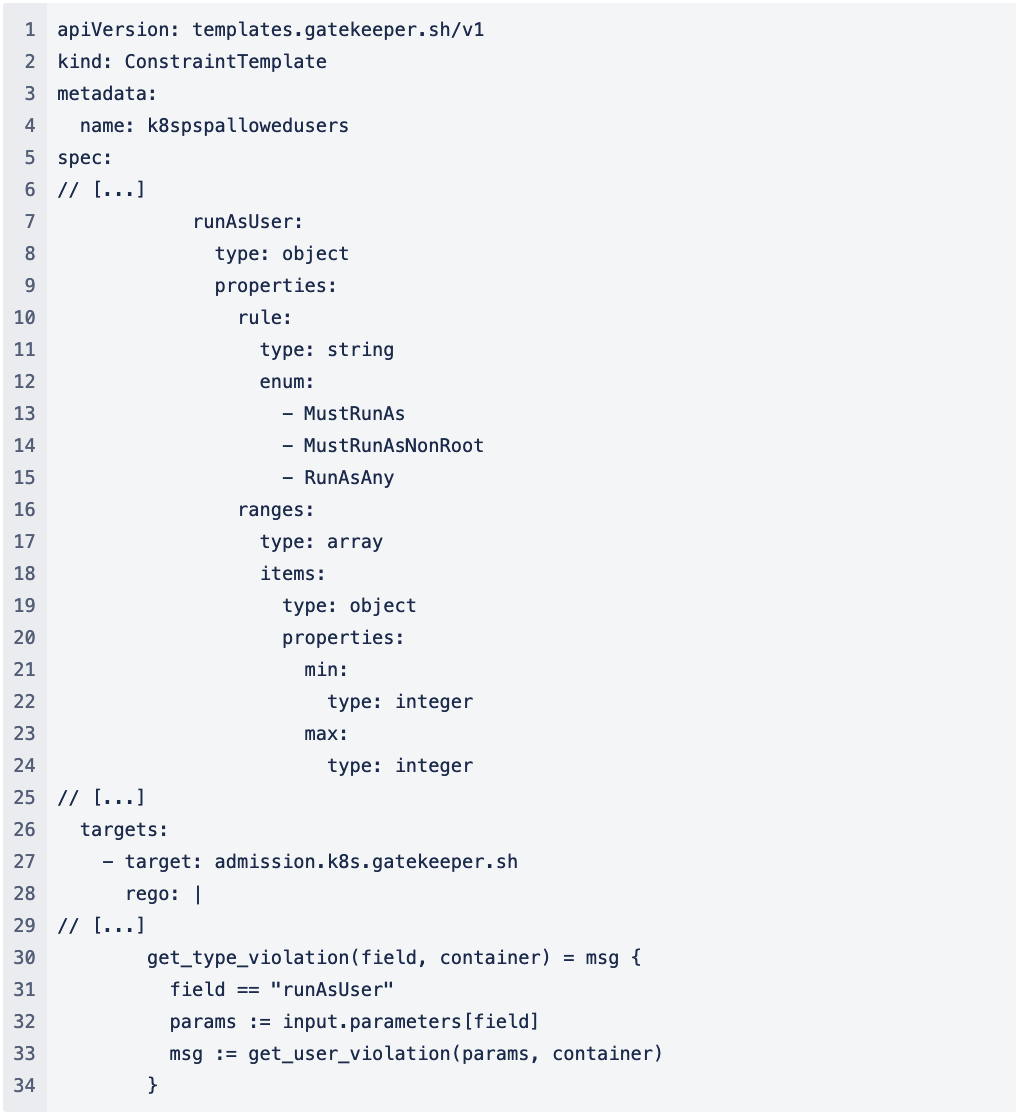 Figure 1: Example Snippet from a Template File partly extracted from [TODO]
Figure 1: Example Snippet from a Template File partly extracted from [TODO]
Figure 1 shows a snippet from a template file taken from the public library of Gatekeeper. We want to point out two different parts: First, between line 7 and line 24 we find the declaration of a variable called “runAsUser“ as an object consisting of an enum and an array of two integers. Second, the rego code is implemented between line 26 and line 33. We use the declared variables here to divide the rules and the definition of the variables.
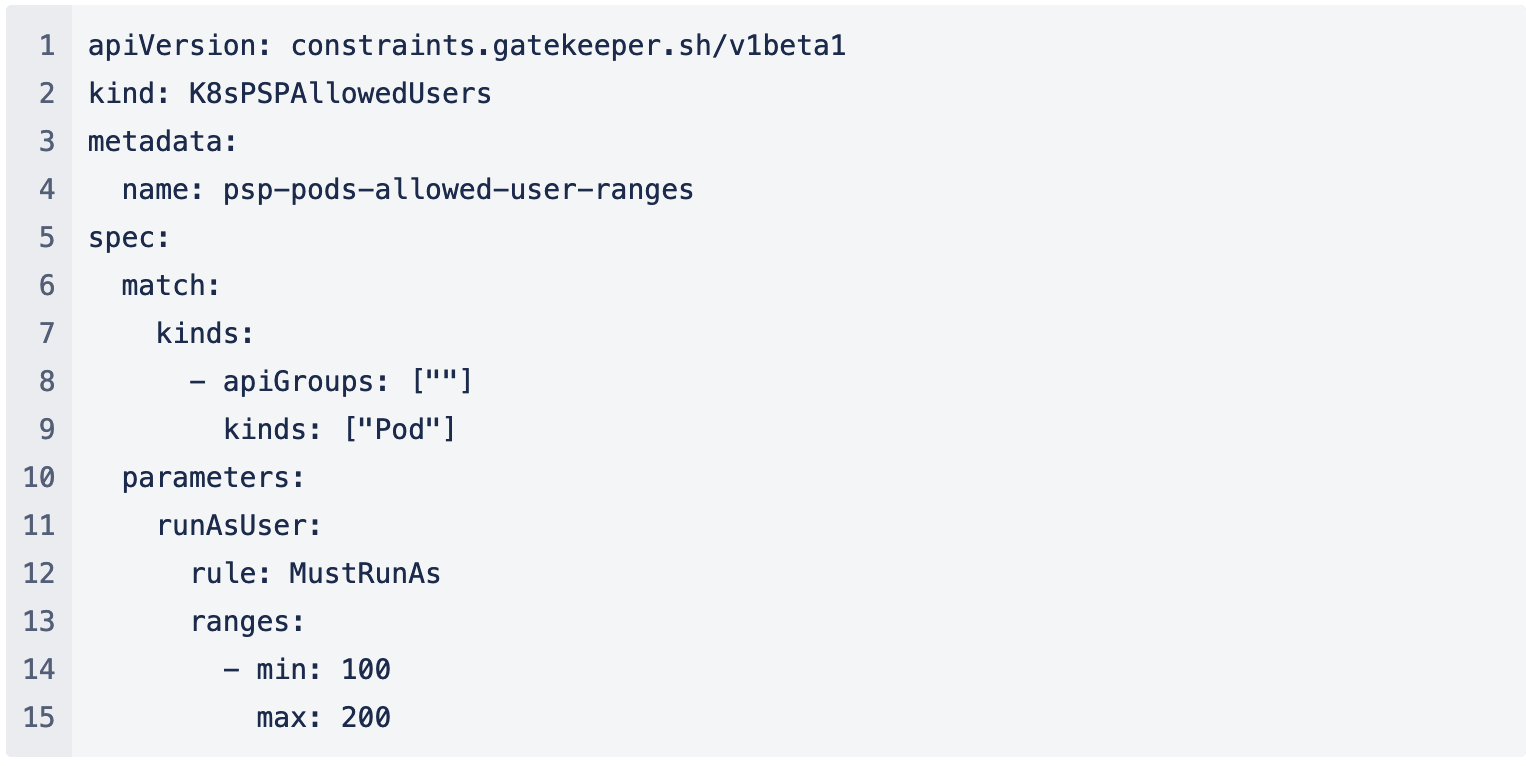 Figure 2: Example Snippet from a Constraint File partly extracted from [TODO]
Figure 2: Example Snippet from a Constraint File partly extracted from [TODO]
Next, we have to define the variables for a target cluster and roll it out. Figure 2 shows an example of a constraint that utilizes the previous template. Lines 7 to 9 define that the constraint will run on the pod-level which means that every pod requires this definition, while lines 11 to 15 are the definition of the variable from the template. If you roll out the template and the constraint in a cluster now, every new manifest requires a suitable security context as the Gatekeeper enforces that the field in manifest is set. Otherwise, the manifest would not be added to etc.
As you can see, you can add templates to several clusters that include adjustable rules and you initialize these rules by using constraints. You should implement rules as code that you can manage through a repository using git. This way you can automate and streamline installation and maintenance, reducing the work load for DevOps.
Gatekeeper allows you to have three different ways of deploying: The standard k8s API calls, customize, and terraform. While the second option is recommended from the Gatekeeper documentation, we recognized that a lot of users try to track the state of their resources. Therefore, we also used terraform with a suitable provider to insert the constraints and templates.

Figure 3 shows an example of a Gatekeeper deployment with Terraform. We can deploy files from public libraries in AWS CodeCommit and can deploy a copy of used Gatekeeper template files in an AWS CodeCommit Repository. Additionally, with the Constraints, we can fetch their differences and deploy changes, when we allow to merge into main after a pull request (PR). This is valuable especially for organizations with strict auditing policies before deployment. When the PR is approved, CodePipeline initiates a CodeBuild instance that runs terraform to roll out changes in templates and constraints.
In a multi-cluster setup where you have to ensure the same setup for more than one cluster, this might be interesting for you as you could change the target cluster with new instances in CodeBuild with the same repository as source. You can implement the deployment in steps, in which the production stage may be updated only when the development stage has also been updated successfully. In addition, different constraints can be used for multiple clusters too.
This was the last part of the blog post series, in which an example deployment for Gatekeeper, its templates, and constraints has been shown. If you require a more overall view on the topic of Admission Controllers, have a look at our other blogpost about this topic. Do not hesitate to contact us as Alice&Bob.Company if you need more information. We would love to assist you.